Endpoint Segmentation Service
Our solution enables fast and secure micro-segmentation in your network, at comparatively low cost and with minimal effort. Once inserted into existing network connections, it immediately provides protection against lateral movement, the spread of malicious code, and the occurrence of unauthorized and unwanted communication. The solution is integrative and fits into the individual system landscape.
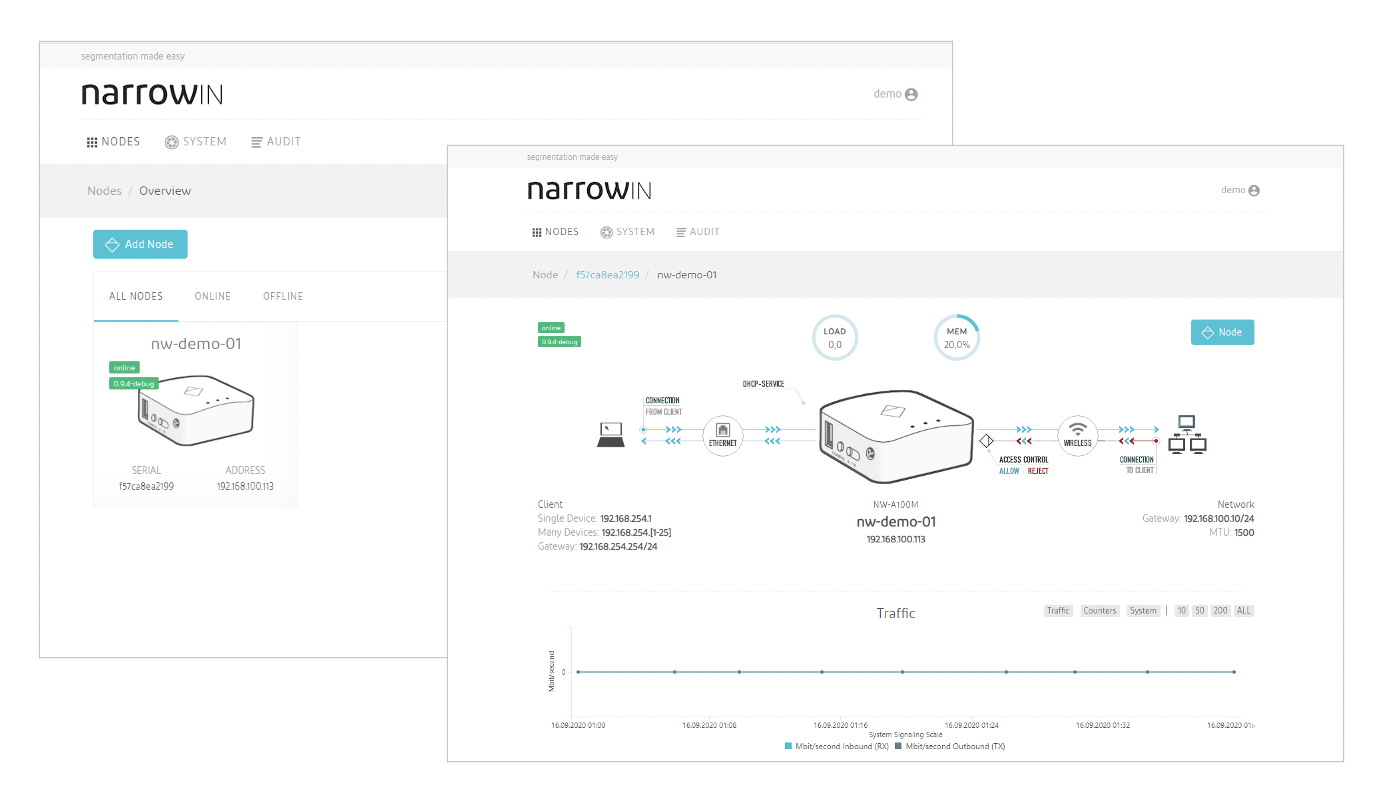
Via an intuitive user interface, the Controller (cloud or on premises) enables simple and efficient management of protected endpoints. Incoming and outgoing connections can be logged and forwarded to your log management solution. This gives you valuable insights into allowed and denied communication within your network segments.
read more
The solution can be implemented immediately without extensive IT know-how using our narrowin nodes. These are inserted between the end device and the network. For larger networks the solution can be implemented on existing switching infrastructure (e.g. Cisco, Aruba or Cumulus). Both options can be configured via the same central management system and thus can be used together.
read more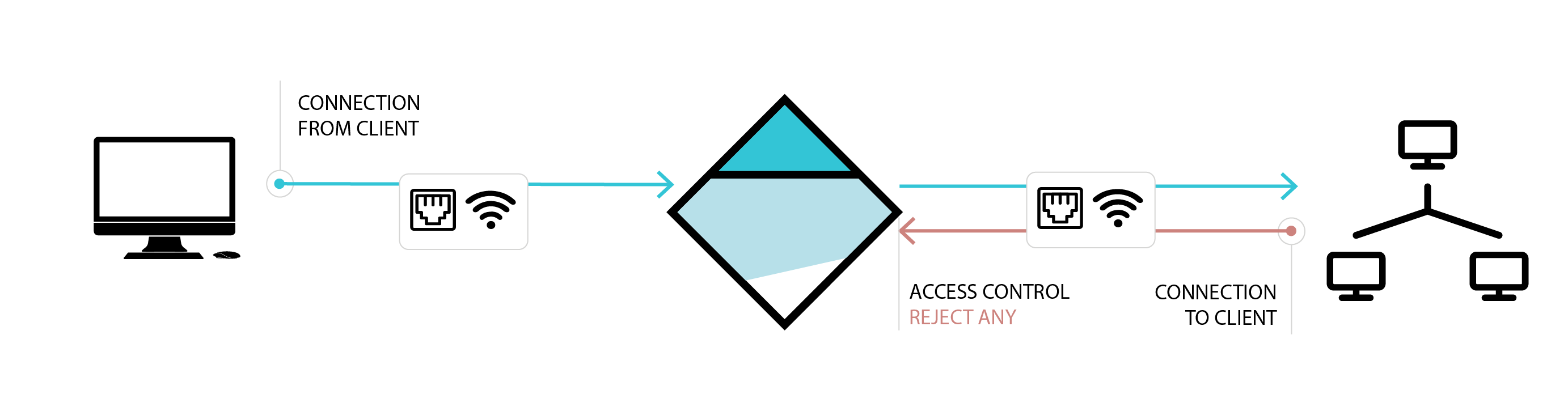
In the default configuration, all incoming communication from the network to the end device is blocked. However, the end device can still communicate with all resources of the network without any restrictions. This ensures that the end device remains fully functional. The same mechanism can also be used to protect the company's infrastructure from the end device (all outgoing communication blocked). Additional necessary access and restrictions can be easily configured.
read more